How Zero Knowledge Architecture Secures Multi Currency Startups in 2025
The New Security Gauntlet for Global Startups
Operating across borders used to be a sign of maturity for a company. Now, it is the default for ambitious startups from day one. This global ambition, however, creates a security minefield. Each country a startup operates in adds another layer to its attack surface, complete with its own financial regulations like GDPR in Europe or MiCA for crypto assets. This patchwork of rules creates inevitable security gaps that are difficult to track and manage.
Compounding this complexity is a threat that has moved from theoretical to imminent: cryptographically relevant quantum computers. These machines are poised to break the encryption standards that currently protect global finance. For a startup, this means that today’s secure data could be harvested now and decrypted later. Preparing for this requires a shift to quantum resistant cryptography, a standard that is no longer optional.
This environment forces startups into a difficult position, caught between conflicting demands for both transparency and privacy. They must navigate:
- Regulatory Pressure: Authorities demand greater transparency for Anti-Money Laundering (AML) and Know Your Customer (KYC) checks.
- Customer Expectation: Users demand absolute privacy and control over their personal and financial data.
Traditional security models, which often rely on centralizing sensitive data, simply cannot resolve this conflict. They were not designed for an era of quantum threats and borderless finance, making truly secure multi currency transactions a significant challenge.
A Primer on Zero-Knowledge Proofs
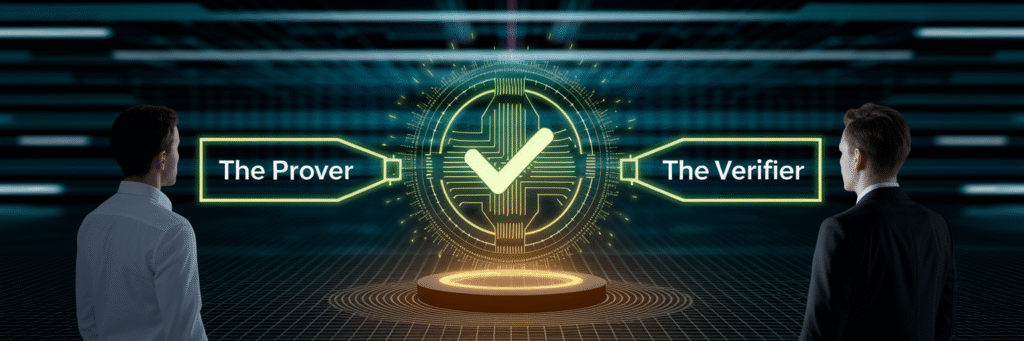
Instead of patching old systems, a fundamentally new approach is needed. This is where Zero-Knowledge Proofs (ZKPs) come in. Think of it like this: you want to prove to a bouncer you are over 21 without showing them your driver’s license, which reveals your name, address, and exact birthdate. A ZKP is the cryptographic equivalent of a special ID card that only confirms your age, revealing nothing else.
In any ZKP interaction, there are two roles. The prover possesses the secret information, like your full bank statement. The verifier, such as a lender, needs to confirm a specific fact, like whether your balance is above a certain threshold. The prover generates a cryptographic proof that confirms the fact is true. The verifier can check this proof without ever seeing the underlying sensitive data. This is the core of zero knowledge proof finance: verification without exposure.
Not all ZKPs are the same. The two most prominent types, ZK-SNARKs and ZK-STARKs, offer different trade-offs that a CTO must consider.
| Feature | ZK-SNARKs (Succinct Non-Interactive Argument of Knowledge) | ZK-STARKs (Scalable Transparent Argument of Knowledge) |
|---|---|---|
| Proof Size | Very small, enabling low on-chain storage costs. | Larger, requiring more data to be stored or transmitted. |
| Trusted Setup | Requires an initial trusted setup ceremony. If compromised, the entire system’s security is at risk. | No trusted setup required (‘Transparent’), enhancing trust and simplicity. |
| Quantum Resistance | Vulnerable to quantum computer attacks. | Inherently resistant to quantum attacks due to its reliance on hash functions. |
| Computational Cost | More intensive for the prover to generate proofs. | Faster for the prover to generate proofs, but more intensive for the verifier. |
The choice between them depends on a startup’s priorities. SNARKs are ideal for minimizing on-chain costs, while STARKs offer future-proof quantum security without the risk of a compromised setup ceremony.
Balancing Compliance and Privacy with ZKPs
With a grasp of what ZKPs are, we can see how they directly solve the compliance and privacy paradox. Instead of treating customer data as a liability to be protected, ZK architecture allows startups to use it for verification without ever holding or transmitting it in a vulnerable state.
Consider AML compliance with ZKP. A startup can generate a proof for a regulator confirming a customer has passed KYC checks against a sanctioned-party list. The regulator receives mathematical certainty that the check was done correctly, but the customer’s name, passport number, and other personal details are never sent or exposed. A paper on SSRN highlights this, explaining that ZKPs enable full compliance without centralizing sensitive information.
This same principle applies to securing multi-currency operations, especially with the rise of stablecoins. Regulatory frameworks like the proposed GENIUS Act in the U.S. demand proof of reserves. Using ZKPs, a startup can prove to an auditor that its stablecoin is fully backed by corresponding assets. The proof confirms the total value without revealing the specific treasury holdings or investment strategies, protecting proprietary financial data.
Ultimately, this approach is about radical data minimization. If sensitive data is never exposed, the damage from a data breach is dramatically reduced. This protects both the startup from regulatory fines and reputational harm, and its clients from financial surveillance and theft.
Building a Quantum-Resistant Financial Stack
Integrating ZKPs is not just about adopting a single technology. It is about building a long-term architectural strategy that anticipates future threats. The quantum computing risk requires a proactive plan, not a reactive fix. This is where a post-quantum financial framework (PQFIF) becomes a vital roadmap for any forward-thinking startup.
This framework, as detailed in proposals like the ‘Post-Quantum Financial Infrastructure Framework (PQFIF)’ submitted to the SEC, is designed to guide the financial industry’s transition to new cryptographic standards. It provides a structured approach to upgrading security without disrupting operations.
Quantum-resistant ZKPs, particularly ZK-STARKs, are a critical pillar of this framework. They provide a verifiable security layer that is secure against both classical and quantum computers, addressing the threat head-on. However, building a quantum-resistant stack is not an abrupt “rip and replace” process. We all know how disruptive that can be.
Instead, the recommended approach is a hybrid model. This involves layering new, quantum-resistant algorithms alongside existing, proven methods. This gradual transition ensures continuous security and stability, strengthening the entire system over time without requiring a complete overhaul from day one. It is a pragmatic path to future-proofing your financial infrastructure.
Practical Steps for ZK Architecture Integration
The theory behind ZKPs is powerful, but how does a startup actually begin implementation? We have to be realistic. The computational costs can be high, and developers with deep cryptographic expertise are scarce. However, the path to adoption is becoming clearer and more accessible.
For founders and CTOs, here are concrete first steps to take:
- Conduct a Data-Flow Risk Assessment. Before writing a single line of code, map out where your most sensitive data flows. Identify the points of greatest exposure, such as KYC onboarding or cross-border payment processing. Focus your initial efforts there.
- Start with a Pilot Project. Do not try to secure your entire system at once. Begin with a small, contained use case, like securing login credentials or a single type of internal transaction. This allows you to demonstrate value and learn without risking core operations.
- Explore ZKP-as-a-Service Platforms. The need for in-house specialists is a major barrier. You can explore emerging solutions designed to abstract away the cryptographic complexity, making integration more accessible. These platforms provide the tools to build ZKP applications without needing a team of cryptographers.
Looking ahead, an exciting development is the rise of Zero-Knowledge Large Language Models (ZKLLMs). This technology allows a startup to run powerful AI models for tasks like fraud detection or market analysis directly on encrypted data. It can then generate a proof that the AI’s output is valid, all without ever exposing the confidential information it processed. This opens a new frontier for secure, privacy-preserving intelligence.
The Future of Trustless Financial Systems
For years, multi-currency startups have been caught in a tug-of-war between regulatory demands, security threats, and customer privacy. Zero-knowledge architecture finally offers a way to resolve this conflict. It enables a system where compliance does not have to come at the expense of privacy.
This marks a fundamental shift toward “trustless” verification. Instead of relying on the reputation of an institution to handle data responsibly, trust is guaranteed by mathematical proof. It is a system where you do not have to trust, you can simply verify.
We believe this is more than just a technology for startups. ZKPs are poised to become a foundational layer for the entire financial industry. Their applications in digital identity, asset tokenization, and secure inter-bank communication are immense. By embracing these principles now, startups are not just protecting themselves. They are building the blueprint for a more resilient, private, and efficient global financial system.